
Understanding the CrowdStrike Crash: What Happened and How to Safely Remove Affected Files
On July 2024, the cybersecurity industry was rocked by the sudden and unexpected crash of CrowdStrike’s systems. As one of the leading providers of endpoint protection, threat intelligence, and cyberattack response services, CrowdStrike’s failure raised significant concerns across the tech world. Here’s a breakdown of what happened and its implications for cybersecurity.
What Happened?
On July 10th, 2024, CrowdStrike experienced a catastrophic system failure that resulted in widespread service outages. The incident disrupted the company’s Falcon platform, which many businesses rely on for real-time threat detection and response. Users reported being unable to access their dashboards, conduct threat analysis, or receive alerts, leaving their systems vulnerable.
The Impact
The immediate impact of the crash was profound. Businesses that depend on CrowdStrike’s services were left exposed to potential cyber threats. The outage also led to a significant loss of trust among clients who rely on the company’s assurances of continuous protection. Moreover, the incident sparked debates about the reliability of cloud-based cybersecurity solutions.
Response and Recovery
CrowdStrike’s response was swift but complex. The company initiated its incident response protocol, involving both internal teams and external experts to diagnose and resolve the issue. Over the next 48 hours, the majority of services were restored, but the road to full recovery involved extensive system checks, data integrity verifications, and enhancements to prevent future occurrences.
Lessons Learned
The CrowdStrike crash underscored several key lessons for the cybersecurity community:
- Redundancy and Resilience: Businesses must ensure their cybersecurity solutions have robust redundancy and resilience mechanisms to withstand unexpected failures.
- Communication: Clear and timely communication with clients during an incident is crucial to maintaining trust and transparency.
- Proactive Measures: Regular system audits, stress tests, and incident simulations can help identify potential vulnerabilities and improve response times.
- Diversification: Relying solely on one cybersecurity provider can be risky. Diversifying security solutions might offer a better safety net against single points of failure.
Future Implications
The CrowdStrike crash serves as a stark reminder of the challenges inherent in cybersecurity. As cyber threats evolve, so too must the solutions designed to counter them. For businesses, this means continually reassessing their cybersecurity strategies, investing in cutting-edge technologies, and ensuring they have robust contingency plans in place.
For the cybersecurity industry, the incident is a call to action to innovate and enhance the reliability of their solutions. It also highlights the importance of collaboration and information sharing to collectively improve defenses against ever-growing cyber threats.
Conclusion
While the CrowdStrike crash was a significant setback, it also provided valuable insights into the current state of cybersecurity. By learning from this incident and implementing stronger safeguards, both providers and users can better prepare for future challenges. In the fast-paced world of cybersecurity, staying vigilant and adaptable is the key to staying secure.
WATCH THIS FOR DETAILS:
Jul 21, 2024Dave explains the Crowdstrike IT outage, focusing in on its role as a kernel mode driver. see: https://amzn.to/3XLJ8kY Get the shirt: https://amzn.to/4bRUgAn Follow me for updates! Twitter: @davepl1968 davepl1968 Facebook: fb.com/davepl
How to Remove CrowdStrike Files from Your System
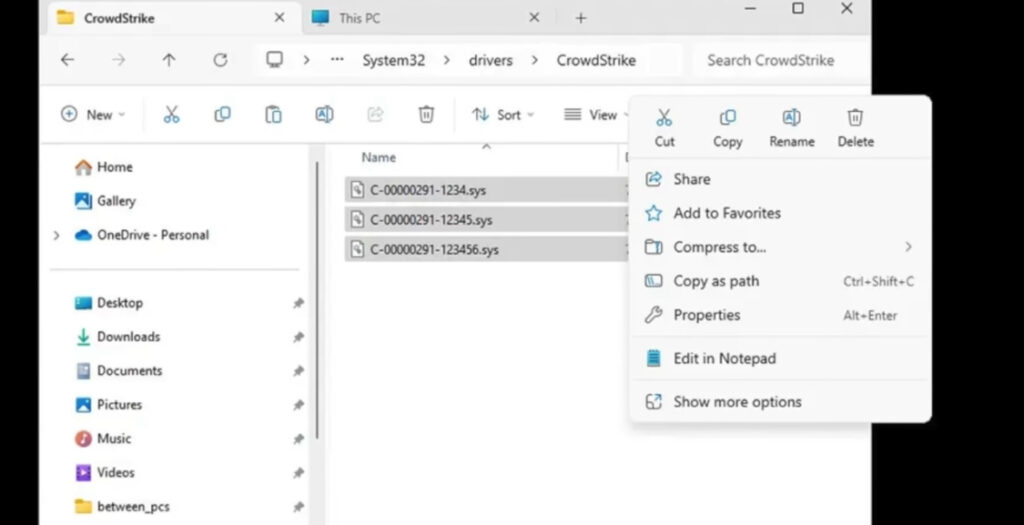
If you need to remove specific CrowdStrike files from your system, follow these steps carefully to ensure a complete and safe removal. The image provided shows three .sys files located in the CrowdStrike folder within the System32 directory. Here’s a detailed guide to help you delete these files.
Important Note:
Before proceeding, ensure that you have administrative privileges on your system and that you fully understand the implications of removing these files, as they may be essential for the proper functioning of CrowdStrike’s cybersecurity software.
Step-by-Step Guide
- Open File Explorer:
- Press
Windows + Eto open File Explorer. - Navigate to
This PC.
- Navigate to the System32 Directory:
- Go to
C:\Windows\System32\drivers\CrowdStrike.
- Locate the Files:
- In the CrowdStrike folder, identify the files you want to delete. In this case, they are:
C-00000291-1234.sysC-00000291-12345.sysC-00000291-123456.sys
- Select the Files:
- Click on each file while holding the
Ctrlkey to select multiple files.
- Delete the Files:
- Once the files are selected, right-click on any of the highlighted files.
- Choose the
Deleteoption from the context menu. - Alternatively, you can press the
Deletekey on your keyboard after selecting the files.
- Confirm Deletion:
- A confirmation dialog may appear asking if you are sure you want to delete the files. Click
YesorOKto proceed.
- Check for Administrative Permissions:
- If prompted for administrator permission, click
Continueor provide the necessary credentials to proceed with the deletion.
- Verify Deletion:
- After deletion, navigate to the Recycle Bin and ensure the files are there.
- Empty the Recycle Bin to permanently remove the files from your system.
Additional Steps (If Needed):
- Disable CrowdStrike Service:
If the files are in use or cannot be deleted, you may need to temporarily disable the CrowdStrike service. - Press
Windows + Rto open the Run dialog. - Type
services.mscand pressEnter. - In the Services window, locate
CrowdStrike Falcon Sensoror similar. - Right-click on the service and select
Stop. - After stopping the service, attempt to delete the files again.
- Safe Mode Deletion:
If you still cannot delete the files, try booting your system into Safe Mode and repeat the deletion process. - Press
Windows + R, typemsconfig, and pressEnter. - In the System Configuration window, go to the
Boottab. - Check
Safe bootand selectMinimal. - Click
OKand restart your system. - Once in Safe Mode, navigate to the files and delete them.
By following these steps, you can effectively remove the specified CrowdStrike files from your system. Always proceed with caution and ensure you understand the role of the files you are deleting, especially when dealing with system-level software.

This is such a detailed and insightful post. I really appreciate the effort you put into explaining everything so clearly.
Well,I really appreciate the kindness! Thank you!