Basics of Cryptography:
Cryptography is the practice of securing information by transforming it into an unreadable format, so only intended parties can access it. Key concepts include:
- Encryption: converting plaintext into ciphertext.
- Decryption: converting ciphertext back into readable form.
- Symmetric encryption: uses the same key for encryption and decryption (e.g., AES).
- Asymmetric encryption: uses a public and private key pair (e.g., RSA).
Cryptography ensures data confidentiality, integrity, and authenticity in digital systems.
History of Cryptography:
Cryptography dates back to ancient times, with early examples such as the Caesar cipher used by Julius Caesar for military communications. It evolved significantly during World War II with machines like the Enigma, which played a crucial role in cryptographic advancements. In the modern era, the rise of computers and the internet led to the development of sophisticated algorithms like RSA and AES, revolutionizing how digital communication is secured.
Timeline of Cryptographic Evolution:
- Ancient Ciphers: Caesar cipher (100 BCE).
- Mechanical Ciphers: Enigma machine (WWII, 1930s-40s).
- Public Key Cryptography: RSA algorithm (1977).
- Modern Algorithms: AES standardization (2001).
Visual Representation of Concepts:
- Symmetric Encryption: Uses the same key for both encryption and decryption.
- Asymmetric Encryption: Two different keys (public and private) are used.
These diagrams help illustrate how cryptography protects sensitive data in a variety of applications, from banking to personal communications.
Here’s a blog-friendly version on cryptography concepts and applications:
The Basics of Cryptography
Cryptography is the science of securing data by transforming it into an unreadable format for unauthorized users. It involves two primary processes:
- Encryption: Converts readable data (plaintext) into unreadable text (ciphertext).
- Decryption: Reverts ciphertext back into readable form using keys.
There are two main types of encryption:
- Symmetric encryption: The same key is used for both encryption and decryption (e.g., AES).
- Asymmetric encryption: Uses a pair of keys (public and private) for secure communication (e.g., RSA).
Historical Evolution of Cryptography
- Ancient Ciphers: The Caesar cipher, used in 100 BCE, was one of the earliest methods for concealing information.
- WWII and the Enigma Machine: One of the most famous cryptographic machines, used by the Germans during World War II, showcased the importance of cryptography in military strategy.
- Modern Algorithms: With the rise of computers, cryptography evolved to include advanced algorithms like RSA (1977) and AES (2001) for securing digital communication.
Types of Cryptographic Algorithms
- Symmetric Encryption Algorithms
- AES (Advanced Encryption Standard): A highly secure standard that uses key lengths of 128, 192, or 256 bits. It’s widely used in banking and government systems.
- DES (Data Encryption Standard): Now outdated, DES was the predecessor to AES but is still a significant milestone in cryptographic history.
- Asymmetric Encryption Algorithms
- RSA (Rivest-Shamir-Adleman): Developed in 1977, RSA uses two keys, one public and one private, making it a popular method for secure data transmission.
- Elliptic Curve Cryptography (ECC): ECC offers the same security as RSA but uses smaller key sizes, making it more efficient for mobile and embedded devices.
- Hash Functions
- SHA (Secure Hash Algorithm): Commonly used to verify data integrity, SHA-256 is the most recognized in cryptocurrency and blockchain applications.
Real-World Applications of Cryptography
- Banking and Financial Transactions:
- AES: Protects sensitive data in banking systems.
- RSA: Secures transactions by encrypting cardholder information during online payments.
- Cryptocurrencies:
- Cryptocurrencies like Bitcoin use cryptographic hash functions (SHA-256) to secure transactions on the blockchain.
- Digital Signatures:
- Asymmetric cryptography forms the foundation of digital signatures, ensuring that documents or transactions are authentic and have not been altered.
Visual Examples
- AES Encryption Process: https://www.geeksforgeeks.org/advanced-encryption-standard-aes/ AES breaks data into blocks and encrypts each using a secret key, ensuring that only authorized users with the key can decrypt the information.
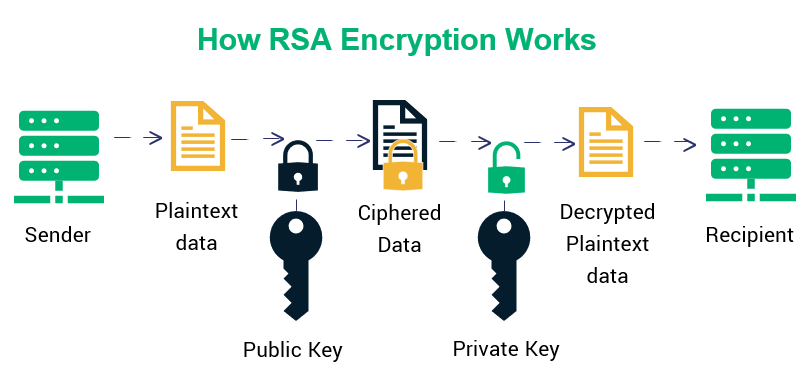
- RSA Encryption Process: https://en.wikipedia.org/wiki/RSA_(cryptosystem)#:~:text=An%20RSA%20user%20creates%20and,who%20knows%20the%20private%20key. In RSA, a public key is used to encrypt data, while a private key decrypts it, providing secure communication over public channels.
The Future of Cryptography
With the rise of quantum computing, traditional cryptographic algorithms like RSA could be vulnerable to new forms of attacks. Researchers are now developing quantum-resistant algorithms to safeguard future data security.
Feel free to explore how cryptography impacts sectors like cybersecurity, online privacy, and digital communication, and why its advancements are crucial in today’s digital landscape!
https://www.youtube.com/user/Simplilearn
Here’s a list of popular blockchain platforms you can use, along with copyable links:
- Bitcoin: https://bitcoin.org
- Ethereum: https://ethereum.org
- Binance Smart Chain (BSC): https://bscscan.com
- Cardano: https://cardano.org
- Polkadot: https://polkadot.network
- Solana: https://solana.com
- Tezos: https://tezos.com
- Avalanche: https://avax.network
- Hyperledger Fabric: https://www.hyperledger.org/projects/fabric
These are some of the most widely used platforms.
A zero-day refers to a software vulnerability that is unknown to the software vendor, and therefore, no patch or fix exists at the time of its discovery. Since the vendor or developers have “zero days” to fix the issue before it can potentially be exploited, this term describes the period of vulnerability and its significance in cybersecurity. The concept of a zero-day vulnerability is a critical aspect of hacking and cybersecurity threats.
Here’s a detailed breakdown of zero-day vulnerabilities, zero-day exploits, and their relation to hacking:
1. Zero-Day Vulnerability:
- A zero-day vulnerability is a flaw or weakness in software, firmware, or hardware that is discovered by hackers or security researchers before the developers are aware of it.
- These vulnerabilities could be anything from weak code, bugs, or faulty logic that can be exploited by attackers to take control of systems, steal data, or disrupt services.
- Once discovered by malicious hackers, this vulnerability becomes extremely dangerous because there is no official patch or fix from the software provider.
2. Zero-Day Exploit:
- A zero-day exploit is the actual method or technique used by hackers to take advantage of the zero-day vulnerability.
- Hackers create and deploy this exploit to target the vulnerability before developers have a chance to issue a patch, which can have devastating consequences.
- Exploits can range from data theft and unauthorized access to full control of systems. These are often part of malware, ransomware, or advanced persistent threats (APTs).
3. How Zero-Day Attacks Work:
- Discovery: A zero-day vulnerability is discovered, often by cybercriminals, who will either exploit it themselves or sell it to other hackers (black market or darknet). Sometimes, security researchers uncover these flaws and report them to developers.
- Exploitation: Attackers develop an exploit that targets this specific vulnerability and launch attacks, either focusing on particular systems or using it to launch a widespread attack.
- Delay in Patch: Since the vulnerability is unknown to the software creator, there’s no immediate patch, leaving the systems defenseless against the exploit for some time.
- Patch Released: Eventually, the software vendor becomes aware of the flaw, develops, and releases a patch to close the vulnerability. The time between the discovery and the patch is critical, as hackers can exploit the vulnerability freely during this window.
4. Hacking and Zero-Days:
- Hackers: Hackers who specialize in finding zero-day vulnerabilities often fall into different categories. There are black-hat hackers, who exploit these vulnerabilities for illegal gain, white-hat hackers (ethical hackers), who notify the software vendor to protect users, and gray-hat hackers, who fall somewhere in between.
- APT Groups: Advanced Persistent Threat (APT) groups often use zero-day vulnerabilities to infiltrate highly secure systems, such as government agencies, corporations, and infrastructure. These attacks are usually covert and target specific organizations.
- Cybercrime Market: Zero-day exploits are valuable in the cybercrime market. Some zero-day vulnerabilities are sold for high prices on the dark web, where criminal organizations, hackers, and even nation-states purchase them for espionage or financial gain.
5. Historical Zero-Day Attacks:
- Stuxnet (2010): One of the most famous examples, Stuxnet used several zero-day vulnerabilities to target Iran’s nuclear facilities. It was a highly sophisticated worm developed by a nation-state and is considered a significant example of a cyber weapon.
- Heartbleed (2014): Though not an intentional zero-day exploit, the Heartbleed bug was a serious vulnerability in the OpenSSL cryptographic software library that allowed hackers to steal data from services using it, including web servers.
- Sony Pictures Hack (2014): Attackers exploited a zero-day vulnerability to breach Sony’s servers, leading to massive data leaks and disruption.
6. Protection and Mitigation:
- Patch Management: Keeping software and systems updated regularly is the first line of defense, but zero-days pose a challenge since patches do not exist immediately.
- Intrusion Detection Systems: Systems that monitor and detect unusual activity can help spot potential exploits, even if the exact vulnerability is unknown.
- Bug Bounty Programs: Many companies run bug bounty programs, offering rewards to ethical hackers who find and report vulnerabilities, reducing the chance of zero-day attacks.
- Network Segmentation: Reducing the damage an attacker can do by limiting access to critical areas of the network through segmentation.
7. Zero-Day Exploit Market:
- A black market exists where zero-day exploits are sold to the highest bidder. This can include governments, intelligence agencies, or criminal organizations.
- Zero-day brokers are intermediaries who buy these exploits from hackers and resell them, making significant profits, especially when dealing with state-sponsored attacks.
Conclusion:
Zero-day vulnerabilities are one of the most dangerous aspects of modern cybersecurity because they are unknown to the software’s creators. Hackers, whether criminal or state-sponsored, can exploit these weaknesses to cause widespread damage. While companies and governments take steps to identify and patch vulnerabilities, the discovery and exploitation of zero-day flaws remain a constant and evolving threat in the digital world.
The white market for zero-day vulnerabilities refers to the legitimate and ethical discovery, reporting, and resolution of software security flaws. It operates within legal boundaries and aims to protect systems, organizations, and users by identifying and fixing vulnerabilities before malicious hackers can exploit them. Here’s how the white market functions:
1. White-Hat Hackers (Ethical Hackers):
- White-hat hackers are security experts or researchers who ethically identify vulnerabilities in software and systems. They work to improve security by responsibly disclosing these vulnerabilities to the relevant software vendors or organizations.
- Their goal is to ensure that vulnerabilities are patched before they can be exploited by malicious actors.
- Many white-hat hackers participate in legal programs and are often rewarded for their efforts.
2. Bug Bounty Programs:
- A major part of the white market is bug bounty programs, where companies and organizations offer financial rewards to ethical hackers who discover and report vulnerabilities.
- How It Works:
- White-hat hackers discover vulnerabilities.
- They report these vulnerabilities through the company’s bug bounty platform or directly to the security team.
- If the vulnerability is valid, the hacker is rewarded, and the company works on a patch or fix.
- Popular Bug Bounty Platforms:
- HackerOne
- Bugcrowd
- Synack
- Many major companies like Google, Microsoft, and Facebook run their own bug bounty programs to ensure the security of their products.
3. Responsible Disclosure:
- Responsible disclosure is the practice of privately informing the vendor or software provider of the vulnerability, allowing them time to fix it before any public announcement is made.
- Once a patch is available or a reasonable time has passed, the vulnerability is publicly disclosed to inform the wider community, helping to protect others from similar issues.
- This practice ensures that vulnerabilities are addressed before they can be exploited, making it a crucial part of the white market.
4. Vulnerability Disclosure Programs (VDPs):
- Many companies and government organizations run vulnerability disclosure programs (VDPs), which allow ethical hackers to report vulnerabilities without fear of legal repercussions.
- VDPs usually have guidelines that define how to report a vulnerability, and they often outline the legal protections for the researchers who participate.
- Examples of VDPs: The U.S. Department of Defense’s Hack the Pentagon program and Microsoft’s Security Response Center (MSRC).
5. Security Research Firms:
- Professional security research firms play a large role in the white market by discovering and responsibly disclosing vulnerabilities on behalf of their clients.
- These firms often have dedicated teams of researchers who analyze software, conduct penetration testing, and look for zero-day vulnerabilities as part of their services.
- Their discoveries are typically disclosed privately to the software vendors or clients they serve.
6. Patch Development and Security Updates:
- Once a vulnerability is reported, the software vendor’s security team works on developing a patch or fix. The time it takes to develop a patch depends on the complexity of the vulnerability.
- After a patch is developed, vendors issue security updates to users and organizations, ensuring their systems are protected against the newly discovered vulnerability.
- Regular patch management and updating systems is a key part of protecting against zero-day attacks in the white market.
7. Legal Framework:
- In the white market, all activities are conducted within the legal framework of cybersecurity laws and regulations. Ethical hackers adhere to guidelines, such as:
- Computer Fraud and Abuse Act (CFAA) in the U.S.
- General Data Protection Regulation (GDPR) in the EU.
- Data Protection Acts in various countries.
- Many companies also require hackers to follow strict rules when testing their systems to ensure that their work doesn’t harm users or compromise sensitive data.
8. Security Conferences:
- Security conferences such as DEF CON, Black Hat, and RSA Conference are hubs for ethical hackers and researchers to present their findings in a responsible and legal manner.
- These conferences encourage collaboration between the cybersecurity community and software vendors to improve global security.
- Often, zero-day vulnerabilities are responsibly disclosed at these conferences, with patches already available or in development.
9. Collaboration with Governments and Organizations:
- Many government agencies, including law enforcement, work closely with white-hat hackers and security researchers to identify and fix vulnerabilities.
- Governments often set up cybersecurity initiatives that incentivize ethical reporting of vulnerabilities in critical infrastructure, such as healthcare systems, energy grids, and financial institutions.
- Some agencies, like the Cybersecurity and Infrastructure Security Agency (CISA) in the U.S., coordinate responses to vulnerabilities that affect large parts of the public.
10. Professional Ethical Hacking Certifications:
- Ethical hackers often pursue professional certifications to demonstrate their skills and commitment to ethical hacking. Common certifications include:
- Certified Ethical Hacker (CEH)
- Offensive Security Certified Professional (OSCP)
- GIAC Penetration Tester (GPEN)
These certifications ensure that security professionals are trained in the latest ethical hacking techniques and understand the legal and ethical implications of vulnerability discovery.
Summary of White Market:
- The white market focuses on ethical vulnerability discovery, responsible reporting, and collaborative efforts between security researchers, companies, and governments to improve overall security.
- By providing incentives through bug bounties and vulnerability disclosure programs, the white market helps prevent zero-day vulnerabilities from being exploited by malicious hackers.
- The ultimate goal of the white market is to make the digital world safer by identifying and fixing vulnerabilities before they can cause harm.
https://www.cisa.gov/known-exploited-vulnerabilities-catalog